Dependable Computing and Fault Tolerance
- tsf -
Our focus is on large and networked computing systems comprising a variety of components (supercomputers to embedded systems) in which software and services play a decisive role. It is important to take into account the evolution of such systems (functional, environmental, technological) involving new threats and classes of faults. Our research addresses four major challenges: mobility, evolvability and autonomy, openness, and reactivity. A key feature is the breadth of faults considered: accidental faults (physical, software) and malicious interaction faults. Our approach combines analytical and experimental methods to meet these challenges.
Architecture (Fault prevention and Fault tolerance)
Fault tolerance software for dynamic distributed systems
The challenge is to tolerate faults despite sources of uncertainty such as the locality of knowledge (no global view) and the asynchrony of distributed nodes.
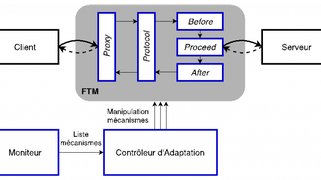
Adaptive fault tolerance
Dynamic adaptation of fault tolerance mechanisms is a means of ensuring the persistence of dependability in the face of changes in the system or its environment.
Safety monitors for critical autonomous systems
This work focuses on autonomous robots and vehicles operating in spaces shared with humans. They implement monitoring mechanisms that can trigger safety interventions when a dangerous situation is detected.
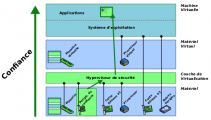
Security architectures
The aim is to design architectures that are resistant to attacks and malicious acts.
Model-based intrusion detection
Our work focuses on intrusion detection in systems for which there are no existing attack bases: critical embedded systems and the Internet of Things. In these cases, intrusions cannot be detected by searching for known attack signatures, and a model-based approach is particularly relevant.
Personal data protection
The challenge is to enable the use of digital applications and services while protecting personal data.
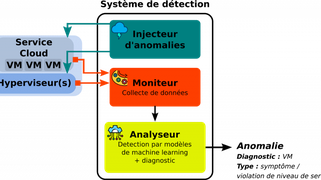
On-line learning-based anomaly detection
This work focuses on the early detection of anomalies affecting services deployed in the cloud.
Multi-core architectures and mission-critical systems
Multi-core architectures introduce a lack of predictability in execution times. Nevertheless, their introduction in mission-critical systems will become essential to meet the growing need for embedded computing power. Our work aims to offer solutions to this problem.
Analysis (Fault removal and Fault forecasting)
Abstractions and models of connected dynamic systems
This work focuses on graphs as models of interaction structures, from an algorithmic point of view.
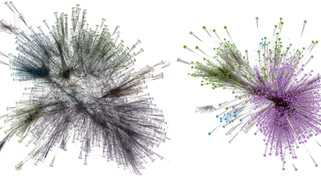
Experimental characterization of social interactions
This work exploits location data from human interaction, for example to deduce mobility models or to study collective decision-making processes.
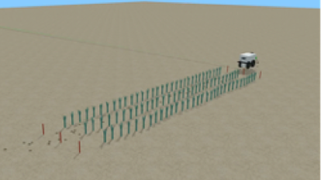
Software testing of stand-alone systems
The focus is on simulation-based testing methods. The system is immersed in virtual worlds, where it is confronted with a wide range of test situations.
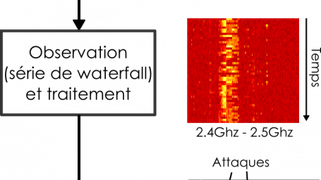
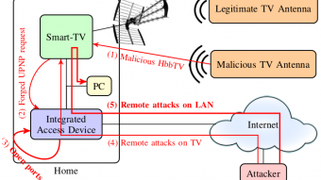
Vulnerability scans and security assessments
This work develops experimental methods for discovering vulnerabilities, and assessing the effectiveness of protection mechanisms against attacks.
Safety arguments and confidence quantification
The aim is to help build a safety case using formalized models. The work is based on Bayesian networks and belief functions (Dempster-Shafer theory).
Head
Scientific executive
ITA contractor
Postdoctoral
PhD
Intern
Partnership guest
Latest publications
2024
Journal articles
Conference papers
2023
Journal articles
Books
Conference papers
Preprints, Working Papers, ...
2022
Journal articles
Book sections
Conference papers
Other documents
Proceedings
Reports
Preprints, Working Papers, ...
2021
Journal articles
Conference papers
Other documents
2020
Journal articles
Conference papers
Other documents
2019
Journal articles
Conference papers
Other documents
Preprints, Working Papers, ...
Softwares, Prototypes and Demonstrators
- SMOF (Safety Monitoring Framework) J. Guiochet, H. Waeselynck, 2018: https://www.laas.fr/projects/smof
- YOUCAN (Hazard model-based analysis with HAZOP-UML.) J. Guiochet, 2018: https://www.laas.fr/projects/HAZOPUML
- Osmosis (Open Source Material fOr Safety assessment of Intelligent Systems), J. Guiochet, H. Waeselynck, 201X: https://osmosis.gitlab.io/index.html
- NFLib is a library created to optimize the computing performance of arithmetic operations performed on polynomes, M.-O. Killijian, C. Aguilar Melchor et al.: https://github.com/quarkslab/NFLIb
- XPIR (Private Information Retrieval for Everyone), M.-O. Killijian, C. Aguilar Melchor et al., 201X: https://github.com/XPIR-team/XPIR
library dedicated to the construction of PIR protocols - MIRAGE, V. Nicomette, R. Cayre et al., 2019, https://homepages.laas.fr/rcayre/mirage-documentation/
a framework for vulnerability analysis and security auditing of connected objects - GEPETO (GEoPrivacy-Enhancing TOolkit), M.-O. Killijian, M. Nunez del Prado Cortez, S. Gambs (Univ. Rennes), 2014 (Diffusion with GIT. License CeCILL-B)
GEPETO is a flexible software that can be used to visualize, sanitize, perform inference attacks and measure the utility of a particular geolocated dataset. The main objective of GEPETO is to enable a data curator (e.g., a company, a governmental agency or a data protection authority) to design, tune, experiment and evaluate various sanitization algorithms and inference attacks as well as visualizing the following results and evaluating the resulting trade-off between privacy and utility. - MARACAS (CBSE Middleware for adaptive fault tolerance), J. C. Fabre, M. Roy, M. Stoicescu, 2014 (Restricted diffusion)
This middleware illustrates how fault tolerance mechanisms can be adapted and combined online. Different types of changes related to the evolution of the resource requirements, the applications, or the fault model during operation, could be at the origin of the dynamic reconfiguration of fault tolerance mechanisms. A set of mechanisms has been developed to show the capabilities of the CBSE approach based a reflective medium to perform agile dependable systems. It is meant to be a proof of concepts. The techniques behind the proposed approach are applicable to many application areas. - ARINC 653 Simulator, M. Cronel, J. C. Fabre, G. Bustamente, R. Palustran, M. Roy: https://github.com/makrin/ARINC653-simulator (Licenses MIT and CeCILL-B, Diffusion with GIT)
A simulator of the executive support ARINC 653 standard for IMA systems has been developed on Unix. It emulates time and space partitionning concepts and also inter-partitions communication mechanisms. - IronHIDE (outil d’analyse des attaques par entrées-sorties), E. Alata, Y. Deswarte, F. Lone Sang, V. Nicomette, (Restricted diffusion)
IronHIDE is an FPGA-based I/O controller dedicated to the analysis of vulnerabilities at the interface between the hardware and software components. This controller has the advantage of interfacing with the PCI-Express bus and can be used to generate valid and invalid requests on the bus to identify potential I/O attacks. - MINOTOR (Monitoring tool for timing and behavioral analysis), O. Baldellon, J. C. Fabre, M. Roy
A model driven distributed monitoring system for timing and behavioral analysis. The tool is based on a formal framework that extends the semantics of Petri nets to be able to execute it online on partial executions and distributed observation environments. - SOUK (Social Observation of hUman Kinetics), E. Alata, R. Akrout, Y. Bachy, A. Dessiatnikoff, M. Kaâniche, V. Nicomette, 2012 (Restricted diffusion)
SOUK integrates a set of algorithms enabling the processing of geo-locates data, the extraction of social contacts, as well ad the analysis and representation of the social interaction networks. - WASAPY (Web Applications Security Assessment in Python), E. Alata, R. Akrout, Y. Bachy, A. Dessiatnikoff, M. Kaâniche, V. Nicomette, 2012 (Restricted diffusion)
The objective of this software is to identify in an automated way web applications vulnerabilities. This is accomplished by performing a combinational scan of the web site and actually exploiting vulnerabilities. Specially crafted requests derived from a grammar are submitted to the application, and the corresponding responses are analyzed using clustering techniques. This approach has two advantages. The first one is the ability of the software to continue its analysis after exploiting a vulnerability. In particular, pages accessible after exploiting the vulnerability can be processed automatically. The second advantage is its ability to identify vulnerabilities that are activated only after performing a particular action sequence on the site. - HAZOP-UML (Risk analysis for the identification and validation of safety requirements), Q.A. Do Hoang, D. Martin-Guillerez, J. Guiochet, D.Powell, 2011 (Restricted diffusion)
HAZOP-UML is a tool for model-based safety analysis. This tool allows to model UML (Unified Modeling Language) sequence and use case diagrams, which are used to generate deviation tables applying the HAZOP technique (HAZard OPerability). - STELAE (Systems TEst LAnguage Environment), R. Guduvan, H. Waeselynck, V Wiels (ONERA), G. Durrieu (ONERA), Y. Fusero (Cassidian), M. Schieber (Cassidian), 2010 (Restricted diffusion)
STELAE is a model-driven environment for the development of tests of avionic systems. It includes customizable graphical and textual editors for abstract test models, checkers, and finally template-based transformations towards code executable on top of a real industrial test platform (the U-Test platform of Cassidian Test & Services). The core part of STELAE is a metamodel capturing a rich set of domain-specific concepts. - STANCE (Structural ANalysis of Counter Examples), T. Bochot (ONERA & Airbus), K. Cabrera, P. Virelizier (Airbus), H. Waeselynck, V. Wiels (ONERA)
STANCE aids in the debugging of Simulink models, when a lengthy counterexample is returned by the model checker. It performs a structural analysis of the model’s paths activated by the counterexample and extracts relevant information to explain the observed violation. STANCE may also be used to guide the model checker toward the search for different counterexamples, exhibiting new path activation patterns and thus new ways to violate the property. - TERMOS (TEst Requirement language for MObile Setting), P. André, Z. Micskei (BUTE), M.D. Nguyen, N. Rivière, H. Waeselynck, 2009 (Restricted diffusion)
TERMOS is a formal language based on UML Sequence Diagrams used for the testing of mobile applications, integrated into UML support technology. The tool contains: (i) a UML profile for the editing of verification scenarios (positive and negative requirements, test purposes) with spatial and event views, (ii) an Eclipse plugin for the automated checking of traces. The checking of traces against scenarios combines graph matching and event order analysis. The graph matching part searches for occurrences of the target sequence of spatial configurations. The event order analysis relies on an automaton-based semantics of sequence diagrams. - MASS (Multi Agent Simulator Software), J.H. Collet, 2007 (Restricted diffusion)
MASS is a simulator based on mobile agents in two or three dimensions. Agents are activated asynchronously with a scheduler, and each one executes a state machine. The software runs on a Windows platform. It has been parallelized to take advantage of multicore processors.
THESIS / HDR
2023
Cyrius Nugier, Thèse: Adaptation d'Outils Cryptographiques pour un Contexte Post-Quantique
2022
2021
Clément Robert, Thèse: Génération et analyse de tests pour les systèmes autonomes
2020
2019
Gilles Trédan, Habilitation à diriger des recherches: Capturer des graphes binaires
2018
2016
Joris Barrier, Thèse: Chiffrement homomorphe appliqué au retrait d'information privé
2015
2014
Jobs / Interships
REJOINDRE
Notre équipe de recherche
Pour plus d’informations sur les offres d’emploi, vous pouvez contacter