Model-based intrusion detection
Our work focuses on intrusion detection in systems for which there are no existing attack bases: critical embedded systems and the Internet of Things. In these cases, intrusions cannot be detected by searching for known attack signatures, and a model-based approach is particularly relevant.
Intrusion detection generally relies on data collected from the observed system's event logs to detect signs of an attack, either by comparing observations with a model of legitimate behavior, or by searching for signatures of known attacks. In this context, we are interested in developing detection techniques adapted to the specific constraints of critical embedded systems (in the automotive and avionics industries) and the Internet of Things.The lack of knowledge about attackers and the absence of attack signature databases in these contexts leads to a preference for model-based approaches.
As part of I. Studnia's thesis, we focused on the detection of malicious traffic between embedded ECUs, particularly on the CAN bus. The constraints of the automotive sector mean that the ECU architecture must not be modified, while allowing for simplicity of implementation at low cost. The advantage is that ECU specifications are available. Based on these specifications, the approach we have developed automatically generates a model of illegitimate message sequences likely to be observed on the bus. This model, used as a reference by the detector, is obtained using language theory. This work has been patented[1]. I. Studnia also won a Renault Innovation Award in 2015.
Another approach aimed at detecting abnormal behavior in embedded applications on modular avionics platforms is currently being explored as part of A. Damien's thesis. Damien's thesis. The pessimistic hypothesis is that a critical avionics application can be corrupted during the integration, operation or maintenance phases. We consider the point of view of a system integrator who does not have the application specifications, but who is responsible for system security. The proposed approach is to build, during the integration test phase, a model of the behavior of the various functions, and to embed this model directly in the system for in-flight detection[2]. Machine learning techniques are being explored to experimentally define indicators at hardware layer level characterizing the security domain of these applications, and to detect any abnormal deviation in operation. Attack injection techniques are also being developed to validate the effectiveness of the solution.
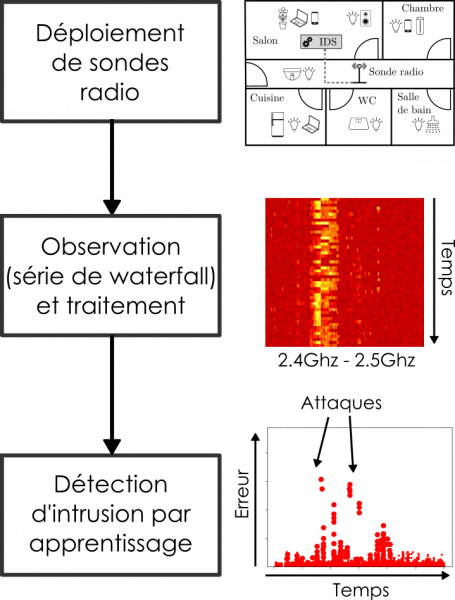
In a less critical context, J. Roux's thesis focuses on intrusion detection in a connected environment. Connected objects are widespread, mobile, heterogeneous and use peer-to-peer connections that are sometimes dedicated and difficult to control, whether in a company or a home. Yet they represent an attractive target for attack, due to the less rigorous development methods used for their design and implementation. The usual approaches based on a centralized gateway targeting standard protocols are not suited to this type of environment (for example, the protocols used by all objects are not necessarily known). The solution we have proposed does not require knowledge of the specification of the protocols used. It is based on the observation of radio activity at physical layer level, covering a broad spectrum of communications (including peer-to-peer exchanges). Detection is based on learning algorithms. To validate the effectiveness of our approach, we deployed our solution in a real environment and carried out attack campaigns[3].
[1] Studnia I., Y. Laarouchi (1), Alata E., Kaâniche M., Nicomette N., Système de détection d’intrusion dans les réseaux véhiculaires
Numéro et date de dépôt du brevet : PCT/FR2015052681 - 2015-10. N° et date de priorité : FR1459640 - 2014-10-08
[2] Damien A., Fumey M., Alata E., Kaâniche M., Nicomette V., Anomaly-based Intrusion Detection for an Avionic Embedded System
Aerospace Systems and Technology Conference (ASTC 2018), 2018
[3] Roux J., Alata E., Auriol G., Kaâniche M., Nicomette V., Cayre R., RadIoT: Radio Communications Intrusion Detection for IoT - A protocol Independent Approach, The 17th IEEE Int. Symp. on Network Computing and Applications (NCA 2018), 01-03 Novembre 2018, Boston,











