Security architectures
The aim is to design architectures that are resistant to attacks and malicious acts.
The aim is to design architectures capable, by construction, of preventing the introduction of intentional faults, or of tolerating such faults. The design of such architectures can take different forms: it can concern software, hardware or communication protocols. The aim of B. Morgan's thesis was to design a multi-level security architecture to guarantee the integrity of a critical software component running on an Intel X86 platform.
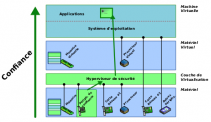
The aim of the secure architecture is to detect attacks running on the processor, whatever the level of privilege of the attack, including a very high level. To achieve this, it comprises two components: a security hypervisor and a specially developed trusted device. The security hypervisor, running at a very high privilege level, is responsible for carrying out integrity tests on the critical component to be protected. However, the mere existence of this hypervisor, however complex, is not enough to guarantee the integrity of the critical software component, as it can be compromised.
En conséquence, l’architecture proposée inclut un matériel spécifique, à base de FPGA, autonome en énergie, connecté simplement sur le bus PCI-Express, et chargé de tester l'intégrité de l'hyperviseur lui-même, grâce à un mécanisme de défi-réponse adapté. Ce périphérique, spécifiquement conçu fournit le socle de confiance de notre architecture et permet, en complément avec l'hyperviseur de sécurité de garantir l'intégrité du logiciel critique surveillé[1].
Another study, currently being finalized, complements this work and concerns ARM architectures and the Android system. G. Averlant's thesis aims to propose a multi-tier architecture on mobile embedded systems (typically SmartPhones), so as to provide the user with a secure environment for executing host applications. Traditional approaches rely on binary partitioning of applications, isolating in particular sensitive applications from other applications. The effectiveness of these approaches is now being challenged by new uses, resulting in the coexistence of applications with heterogeneous levels of security confidence. The architecture proposed in this thesis takes into account the current state of applications running on the smartphone to authorize or not the execution of an application for which a certain number of conflicts are declared. For example, a critical application (e.g. banking) may require that no other application be running at the same time. Other, lighter constraints may simply concern the use of certain resources: application A will only run if resource R is not currently being used by application B. All these constraints are specified in a "secure manifest" which complements the usual Android application manifest. This fine-grained policy is the first contribution of this work, the other being the design and implementation of a security architecture enabling this policy to be implemented within an Android smartphone. This multi-level architecture involves a hypervisor and modifications to both the Android framework and the system kernel (Linux)[2].
Finally, another complementary approach aimed at specifically protecting communication protocols from reverse engineering was explored as part of J. Duchêne's thesis, in collaboration with the DGA.Protecting communication protocols is essential today. When cryptography is too costly in terms of resources or deployment, protocol obfuscation can be an interesting solution. Until now, most work on protocol obfuscation has been carried out with the aim of bypassing protection mechanisms such as firewalls or intrusion detection systems. The originality of J. Duchêne's thesis contributions is that obfuscation is designed to defeat communication protocol reverse engineering tools. Original obfuscation techniques, applied directly to the communication protocol specification, which can be very easily diversified and deployed, have been proposed and tested in this work[3].
[1] Morgan B., Alata E., Nicomette V., Kaâniche M., Averlant G., Design and implementation of a hardware assisted security architecture for software integrity monitoring. The 21st IEEE Pacific Rim Int. Symp.on Dependable Computing (PRDC 2015), Zhangjiajie (Chine), 201
[2] Averlant G., Alata E., Kaâniche M., Nicomette V., Mao Y., SAAC: Secure Android APplication Context - A runtime-based Policy and Its Architecture, The 17th IEEE Int. Symp. on Network Computing and Applications (NCA 2018), 01-03 Novembre 2018, Boston
[3] Duchêne J., Alata E., Nicomette V., Kaâniche M., Le Guernic C., Specification-based protocol obfuscation, 48th IEEE/IFIP Int. Conference on Dependable Systems and Networks (DSN-2018), 25-28 Juin 2018, Luxembourg











