Vulnerability scans and security assessments
This work develops experimental methods for discovering vulnerabilities, and assessing the effectiveness of protection mechanisms against attacks.
The development of rigorous, automated experimental methods for identifying vulnerabilities that could be exploited by attackers, and for analyzing the effectiveness of protection mechanisms (firewalls, intrusion detection systems, etc.) is a major challenge, particularly in the case of new virtualized infrastructures and the Internet of Things.
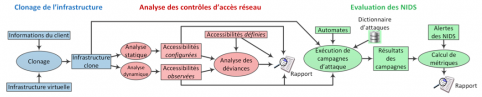
As part of T. Probst's thesis and the SVC future investment project, we studied the case of infrastructures virtualized in clouds, with the aim of automating the analysis and evaluation of network security mechanisms deployed in these infrastructures. This work resulted in the definition and implementation of an original method structured in three phases, taking advantage of the benefits of the cloud to automate the end-to-end audit process:
- Cloning of the customer's virtual infrastructure in operation, whose security is to be assessed.
- Static and dynamic analysis of accessibilities between virtual machines, and detection of any inconsistencies in the configuration of these mechanisms[1].
- Automated generation of attack campaigns for the evaluation of network intrusion detection systems, using the accessibilities identified[2].
A prototype on a Vmware platform was developed and used to validate our method.
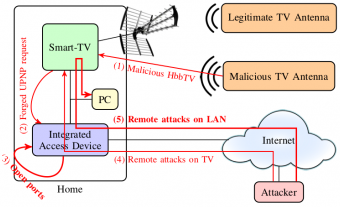
As part of Y. Bachy's thesis, we focused on the vulnerability analysis of consumer equipment connected to the Internet, which has generally not been designed with computer security in mind. Our work has resulted in the development of a comprehensive, generic method combining risk analysis and experimental techniques, enabling us to carry out a vulnerability analysis of such equipment and propose protective countermeasures. Two case studies were considered: ADSL "boxes"[3] and connected TV sets[4], taking into account a panel of products from different suppliers.
Two case studies were considered: ADSL "boxes" and connected TV sets, based on a panel of products from different suppliers. In both cases, we focused on analyzing the security of these devices' access networks and associated protocols (local loop for ADSL boxes, HbbTV protocol for TV sets), which are attractive targets for attackers (Figure 8). We have been able to identify several security flaws and demonstrate technically that these vulnerable devices are likely to affect the security of other systems interacting with them, for example in our homes containing more and more connected objects.
[1] Probst T., Alata E., Kaâniche M., Nicomette V., An Approach for the AUtomated Analysis of Network Access Controls in Cloud Computing Infrastructures, 8th Int. Conference on Network and System Security (NSS 2014), 15-17 Octobre 2014, Xi’an (Chine), 2014
[2] Probst T., Alata E., Kaâniche M., Nicomette V. Automated Evaluation of NIDS in Cloud Computing Virtual Infrastructures. 11th European Dependable Computing Conference (EDCC 2015), 2015
[3] Bachy Y., Nicomette V., E. Alata, Kaâniche M., J.-C. Courrèges. Security of ISP Access Networks: practical experiments. 11th European Dependable Computing Conference (EDCC 2015), 7-11 Septembre 2015
[4] Bachy Y., Basse F., Nicomette V., Alata E., Kaâniche M.,Courrèges J.-C., Lukjanenko P., Smart-TV Security Analysis: practical experiments. 45th IEEE/IFIP International Conference on Dependable Systems and Networks (DSN-2015),Juin 2015, Rio de Janeiro (Brésil)











