Department risc
Trustworthy Computing Systems and Networks
The RISC "Réseaux, Informatique, Systèmes de Confiance" department aims to develop innovative solutions for the design, dimensioning, architecture, analysis, supervision and operational deployment of complex communicating networks and systems and associated applications. Our aim is to contribute to the advancement of knowledge both in terms of theoretical foundations and methodological approaches based on formal and experimental methods, as well as their practical implementation.
head
Research challenges, themes and objectives :
Adaptation and Autonomy
Computer systems are being designed to interact with other systems, to be deployed on a virtualized infrastructure, to be used on a very large scale and in an open, connected environment. Operators need to consider resource sharing and cooperation to meet real-time service demands. Criticality needs to be considered both at the mission or outsourced business process level, and at the deployment infrastructure level.
Players in this field have to cope with increasing complexity linked to heterogeneity, both at infrastructure and process (also called application) levels. The Internet's distributed architecture and massive interconnection, subject to the non-determinism of interactions, makes design and management difficult. For communication networks in particular, autonomy is a key challenge of the highest priority, both for the research community and for industrial players and the international working groups that bring them together. This term can be found under various nomenclatures such as the ETSI working group "Zero touch network & Service Management (ZSM)" [Sprecher'2018] or the concept of self-driving networks [Jacobs'2018].
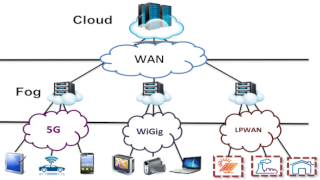
In this context, the locks we are considering are related to the joint and consistent consideration of functional (generic for different domains or for a given domain, or mission-specific) and non-functional (confidentiality, security, quality of service, cost in energy consumption or budget) properties (or requirements) of systems. Challenges concern the management of dynamic adaptation (in the operational phase) of systems to variations in functional and non-functional requirements, and to changes in deployment infrastructure constraints (such as for hybrid environments like IoT/M2M, Fog Computing, 5G, and satellite).
[Sprecher'2018] N. Sprecher, IEEE Softwarization, November 2018 ETSI ZSM Architectural Framework for End-to-End Service and Network Automation. https://sdn. ieee.org/newsletter.
[Jacobs'2018] A. Jacobs et al. Refining Network Intents for Self-Driving Networks. ACM SIGCOMM Computer Communication Review (CCR) 2018.
Scalable distributed systems
With five different contributions, the distributed systems axis covers 2 teams. These approaches cover a wide range of execution models, from the most homogeneous (GPGPU) to the most heterogeneous (opaque cloud). There is a similar variety of theoretical perspectives: topology, linear programming, probability. Numerical simulation and experimental deployment complete the department's toolbox.
The problems targeted are equally diverse: parallelization (i.e. controlling how to distribute a task), scheduling (i.e. how to distribute constrained tasks), monitoring (i.e. how to collect information on the state of computing units and their network conditions). One application spectrum is particularly dominant: AI and its distributed variant, federated AI. Less massively represented, certain applications focus on IoT and planning.
Network and service virtualization
The softwarization of infrastructure and the virtualization of communication networks (and network functions) is a strategic direction for meeting the various technical and socio-economic requirements imposed by emerging systems. It's a direction that interests both the research community and industrial players grouped together in international working groups (ETSI, notably in Europe, and W3C). Current technological solutions are moving in the direction of convergence between the world of information processing, which has seen the advent of "cloud computing" and "service computing" technology for over a decade, and the world of telecommunications, which in recent years has been promoting the softwarization and virtualization of network services and functions (SDN/NFV).
Trusted AI
Artificial intelligence (AI) algorithms and data-driven learning models are increasingly used in all fields. A first strand of our work aims to take advantage of the latest advances in AI to improve the resilience and quality of service of networks and IT systems in various fields (monitoring, anomaly and intrusion detection and diagnosis, testing, etc.). The second part tackles fundamental questions linked to the trust that can be placed in systems using these algorithms, taking into account the constraints specific to these algorithms (opacity, non-determinism, sensitivity to training data, etc.). The challenges lie in finding solutions to improve the explicability of these algorithms, their verification and testing, their protection against attacks aimed at modifying their behavior, or simply at reproducing them illegitimately, and finally the justification of the associated level of trust.
Security, privacy
Cybersecurity :
Our work focuses on end-to-end system security, and covers hardware security, operating system kernel security, application security, the security of connected objects and in particular those of their communication protocols, the security of future-generation networks (in particular 5G and 6G cellular networks) and the cloud, which differ from current communication architectures through general softwarization and virtualization.
Privacy:
In the context of work on the transparency of algorithms used by online platforms, we are interested in how these algorithms exploit user data to produce their decisions.
Systems engineering
The questions addressed in the context of systems engineering (SE) concern:
- The need to master the development process, get experts and stakeholders to cooperate, integrate practices, reconcile points of view, get different models to talk to each other, find a common optimum.
- This requires work on the product and the process (analysis, methods, tools): requirements engineering, process engineering (requirements elicitation, design, V&V, certification, maintenance, service withdrawal, etc.), integration/alignment with standards (system engineering, project management, quality, safety, etc.), modeling (product, process, quality, safety, etc.), model integration, performance measurement, indicators, quality measurement, process engineering (technical and project/agility), simulation and prototyping, design to X, SI deployment in SMEs, etc.
Real-time systems
The notion of real-time system is attached to reactive systems, most often embedded, for which correction does not simply depend on the results or messages they exchange, but also on the moment when these results are produced. Temporal aspects are not the only ones involved in this context. Other types of constraints also need to be considered, such as the system's criticality (reliability, security, etc.) or its embeddability (i.e. its ability to be implemented within constraints on computing power, memory or energy use, etc.). Finally, we also seek to design solutions that make systems more robust and predictable.
Real-time systems represent a cross-disciplinary area of research within the RISC department. We approach the study of these systems according to several complementary objectives: (1) reliability, with the study of techniques increasing resilience and adaptation capacities, for example through specific reconfiguration mechanisms; (2) security, with the design of methods to counter attacks specific to real-time systems; (3) and finally predictability, with the study of new scheduling methods and new analysis techniques, targeting in particular multi-core and/or heterogeneous architectures.
AREAS OF
RESEARCH AND APPLICATIONS
Our research targets systems and applications with demanding requirements in terms of quality of service, time constraints, dependability, resilience or security.
DISCIPLINARY FIELDS
COVERED IN OUR DEPARTMENT
DEPARTMENT TEAMS
The RISC department's activities are carried out by four teams whose research fields are complementary and cover the various challenges linked to the heterogeneity, dynamicity and criticality of processing and communication infrastructures and systems.

trust
A computing system is said to be "trustworthy" if it delivers a service in which users can have justified confidence. The TRUST team is interested in the methods, tools and processes that enable trust to be justified. *TRUST was created …
Latest publications
2025
Journal articles
Book sections
Conference papers
Other documents
Reports
Preprints, Working Papers, ...
Céline Comte, Isaac Grosof. Graph-Based Product Form. 2025. ⟨hal-04956887⟩
2024
Journal articles
Books
Conference papers
Other documents
Proceedings
@softwareversion
Reports
Preprints, Working Papers, ...
2023
Journal articles
Books
Erwan Le Merrer, Gilles Trédan. What is a black box algorithm?. 2023. ⟨hal-03940259⟩
Conference papers
Other documents
Claude Baron. C'est quoi une dashcam ? A quoi ça sert ?. 2023, pp.8. ⟨hal-04014494⟩
Proceedings
Reports
Preprints, Working Papers, ...
THESIS / HDR
2025
2024
Zheng Zhou, Thèse: IoT omniprésent grâce aux communications spatiales
2023
Clément Cassé, Thèse: Prévision des performances des services Web en environnement Cloud
2022
2021
Kokouvi Benoit Nougnanke, Thèse: Vers un management basé ML des Réseaux SDNs
Clovis Anicet Ouedraogo, Thèse: Sur la gestion de la QoS dans les plates-formes IoT compatibles NFV
2020
Quentin Ricard, Thèse: Détection autonome de trafic malveillant dans les réseaux véhiculaires
Imane Oussakel, Thèse: Métrologie et management des réseaux cellulaires 4G/5G
Santiago Duran, Thèse: Allocation de ressources avec environnements observables et non-observables
2019
2018
Nicolas Seydoux, Thèse: Vers une gestion intelligente des données de l'Internet des Objets
Gilles Roudiere, Thèse: Détection d'attaques sur les équipements d'accès à Internet
2017
2016
Ikbel Guidara, Thèse: Choix efficace du temps et du QoS pour la composition du service
2015
DEPARTMENT NEWS