Trustworthy systems: foundations and practices
- trust -
TRUST's research is organized around six main themes that combine today's challenges - such as critical autonomous systems or trustworthy AI - with recurring themes such as cybersecurity, real-time computing, systems engineering, and theoretical computer science.
Critical autonomous systems
The stakes for the safety of autonomous systems are high: the deployment of driverless cars and all kinds of advanced robots depends on the solutions that can be provided. The team's work focuses on methods for analyzing such systems.
Trustworthy AI
Machine learning models are increasingly used in different types of systems, e.g., to implement a perception function in an autonomous system or to provide personalized recommendations in a social network. These examples illustrate different notions of trust that are being explored within the team.
Security and privacy
Attackers target a wide range of systems and exploit vulnerabilities at all levels (human, software, hardware). Our research reflects this diversity of threats by studying vulnerabilities and protection mechanisms in different application environments.
Real time computing
Real-time computing concerns reactive systems, most often embedded, that must satisfy time constraints. Typically, other constraints have to be added, such as the coexistence of tasks of different criticality, and the embeddability of the system in terms of computational power, memory usage, or energy consumption. Our work seeks solutions to satisfy these constraints in a predictable and robust way, targeting implementations on modern multicore and/or heterogeneous microprocessors.
System assurance
This theme covers research into analysis methods and engineering processes for trustworthy systems, often under the constraints of quality standards and certification.
Algorithms and formal methods
This work addresses fundamental problems by searching for algorithms that provide formal guarantees. The algorithms fall into two broad categories: fault tolerance algorithms and automated verification algorithms.
Head
Scientific executive
ITA contractor
Postdoctoral
PhD
Intern
Scientific guest
Partnership guest
Latest publications
2025
Journal articles
Book sections
Conference papers
Preprints, Working Papers, ...
2024
Journal articles
Books
Conference papers
Other documents
Proceedings
@softwareversion
Preprints, Working Papers, ...
2023
Journal articles
Books
Erwan Le Merrer, Gilles Trédan. What is a black box algorithm?. 2023. ⟨hal-03940259⟩
Conference papers
Other documents
Claude Baron. C'est quoi une dashcam ? A quoi ça sert ?. 2023, pp.8. ⟨hal-04014494⟩
Proceedings
Preprints, Working Papers, ...
2022
Journal articles
Book sections
Conference papers
Proceedings
Reports
Preprints, Working Papers, ...
2021
Journal articles
Conference papers
@softwareversion
Reports
2020
Journal articles
Conference papers
Other documents
Reports
Yann Argotti. Activity Report: PhD 2nd Year. LAAS - CNRS; Renault Software Las. 2020. ⟨hal-02491526⟩
Preprints, Working Papers, ...
Projects
- Institute for Cybersecurity in Occitanie (ICO) (2022-2026)
- ANITI - co-chair of “Towards the certification of ML-based systems" (in collaboration with ONERA) (2019-2023)
ANITI 2.0 - co-chair of “Embeddability and safety assurance of ML-based systems under certification" (in collaboration with Airbus and ONERA) (2024-2028)
- IRT Saint Exupéry's Project Cyber Space Simulation (CSS) (2023-2026)
- PEPR cybersecurity / Project Superviz: Supervision and orchestration of security (2023-2027)
- PEPR cybersecurity / Project REV: Vulnerability research and exploitation (2023-2027)
- Project BPI GEOSUR: Development and certification of trustworthy geopositioning systems for autonomous robots (in collaboration with RAP team) (2023-2026)
- Project ANR IDROMEL (coordinator): Improving the Design of secure systems by a Reduction Of Micro-architectural Effects on side-channeL attacks (2021-2025)
- Project ANR EOS: Decision support for active obsolescence management of systems (2022-2026)
- Project ANR PACMAM (coordinator): Passive or ACtive Monitoring and Auditing of Models (2024-2028)
- Project INSA Safe-AML (coordinator): Trustworthy diagnosis and prognosis for Acute Myeloid Leukemia using multimodal machine learning
- CIFRE contracts with Renault (2021-2024), EXPLEO (2022-2025), Thalès (2023-2026), EDF (2023-2026), Airbus (in collaboration with ROC team) (2023-2026), AMpere (2024-2027)
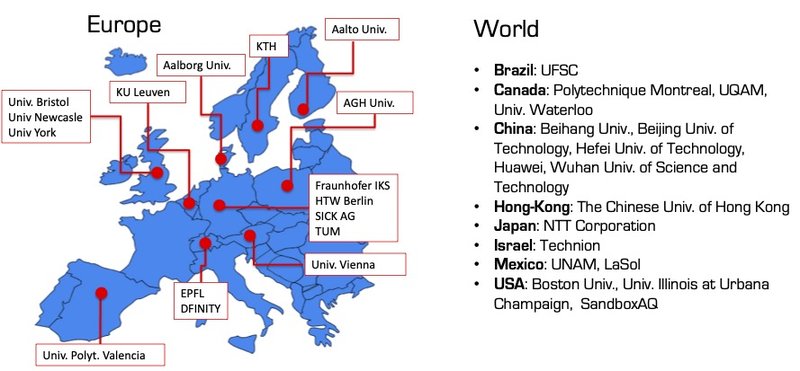
International collaborations
Tools, Prototypes and Demonstrators
- Fiacre: Fiacre is a formally defined language for compositionally representing both the behavioral and timing aspects of embedded and distributed systems, for formal verification and simulation purposes. A dedicated compiler (frac) allows the analysis of Fiacre models using the Tina toolbox. https://projects.laas.fr/fiacre/
- Hippo: Hippo provides a runtime engine for Fiacre. It generates code for embedded real-time applications to enforce their temporal safety. https://projects.laas.fr/hippo/
- MIRAGE: Mirage is a modular framework dedicated to the security analysis of wireless communications. https://github.com/RCayre/mirage
- OASIS: This framework lets you easily patch the firmware of Bluetooth Low Energy controllers to embed intrusion detection mechanisms. It works on several major families of controllers (broadcom and nordic), but requires adaptation for other families. https://github.com/RCayre/oasis
- QasTor (post-Quantum Attribute-based Streaming Through Onion Routing): QasTor proposes an anonymized routing protocol for massive livestreaming, based on post-quantum primitives. This research prototype is currently being valorized by Toulouse Tech Transfer and has been patented.
- Side-channel attacks platform: The platform consists of two attack benches (the first for rapid prototyping, the second more precise to improve measurement quality), and provides a suite of tools for the analysis of leakages and the hardening of targets.
- SMOF (Safety Monitoring Framework): SMOF interfaces with the NuSMV model-checker to synthesize safety monitoring rules from behavioral models. https://www.laas.fr/projects/smof/
- TAF (Test Automation Framework) : TAF takes as input a structured data model with semantic constraints. It generates a sample of data that conforms to the model, combining random generation and constraint solving with Z3. https://www.laas.fr/projects/taf/
- Tina : The TINA toolbox is a set of tools for the edition and analysis of time Petri Nets and their extensions. In particular it can handle Time Petri Nets (TPN), priorities, inhibitor arcs, and an extension of TPN with data handling called TTS. https://projects.laas.fr/tina/
- YOUCAN : YOUCAN is the support tool for the HAZOP-UML method, which combines HAZOP (Hazard Operability) risk analysis and scenario description in UML (Unified Modelling Language). https://www.laas.fr/projects/HAZOPUML/
OTHER TEAMS OF DEPARTMENT
Jobs / Interships
REJOINDRE
Notre équipe de recherche
Pour plus d’informations sur les offres d’emploi, vous pouvez contacter