Department risc
Trustworthy Computing Systems and Networks
The RISC department’s research activities focus on complex information processing and communication systems, which are ubiquitous in daily life and critical across all industrial sectors. Our research aims to achieve methodological advancements to master these systems while meeting stringent requirements in terms of temporal constraints, quality of service, dependability, and cyber-security. The department develops methods, models, and tools, as well as architectures and services for embedded, autonomous, and adaptive critical networks and systems.
head
Scientific Themes and Challenges
Cyber-security
The cyber-security of systems and networks is now a fundamental challenge. The RISC department addresses this theme through multiple scientific axes and across various application domains. One of the department’s strengths is its ability to approach information system security from three complementary perspectives: software security, hardware security, and network security. The proposed security solutions can thus address both software (applications or operating systems, such as in critical embedded systems or IoT devices) and hardware (e.g., cryptographic mechanisms integrated directly into architectures supporting in-memory computing). This cross-cutting vision of information system security is a significant asset, given the strong interdependence between software and hardware in modern computing systems.
In the field of network security, the department explores multiple complementary aspects. It has developed strong expertise in intrusion detection using unsupervised learning models, a focus maintained for many years, and more recently in the generation of synthetic training data. These efforts are conducted in collaboration with industry partners, enabling the integration of the laboratory’s scientific results into commercial security products. Other notable work focuses on the security of IoT communication protocols and their lower layers, addressing both offensive and defensive approaches. These contributions have been published in major security conferences in recent years.
Virtualization and Softwarization
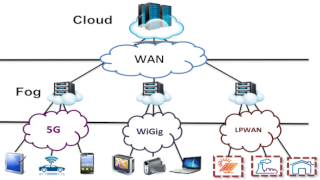
In the era of resource virtualization—extending from cloud servers to the edge of communication infrastructures—the range of possibilities has expanded significantly. However, these advancements come with unprecedented complexity, making the design, planning, deployment, and monitoring of communication networks and their applications increasingly challenging. The boundary between cloud application resources and the communication networks that interconnect them is becoming increasingly blurred. Our research revolves around two complementary themes:
First, we study the Cloud Continuum, which encompasses all interconnected cloud environments, including edge infrastructure and hybrid systems, particularly those related to the Internet of Things. Our contributions have explored new approaches for monitoring applications, data centers, and Internet exchange points, aiming to enhance the autonomy of communication systems.
Second, our research focuses on the orchestration of application and network services to optimize their delivery. We are particularly interested in the dynamic description, discovery, composition, and configuration of services, leveraging IoT service virtualization and the optimal placement of virtualized network functions (VNFs) and their slices, up to their deployment. This work also extends to multi-domain environments, where interconnection and orchestration between heterogeneous infrastructures present new challenges in terms of consistency, compatibility, performance, and resource management.
Toward Trustworthy and Frugal Artificial Intelligence
Over the past decade, methods grouped under the umbrella of artificial intelligence have achieved spectacular results in numerous fields. However, deploying these algorithms requires guaranteeing properties that go far beyond traditional performance criteria, particularly to ensure their safety and reduce their ecological impact.
The RISC department emphasizes trust and frugality in AI algorithms. Trust is addressed through two complementary aspects: transparency in AI models, essential for understanding and justifying their decisions, and runtime monitoring of AI model behavior. Frugality, on the other hand, aims to design algorithms that consume fewer data, computational resources, or energy.
While AI provides tools to address some of the problems studied by the department, we also highlight an inverse movement: traditional departmental tools are applied to improve AI, both at its core and in its implementation and integration as a system. RISC researchers have combined their AI expertise with experience in dependability, computer networks, and stochastic modeling.
Analysis and Engineering of Critical Systems
The concepts of analysis and systems are central to the research of all LAAS departments, as reflected in the laboratory’s acronym. Within the RISC department, we address these issues by focusing on critical systems, whose failures or violations of operational constraints can have severe consequences. We also consider how these systems are designed, validated, and scaled, hence the use of the term engineering. In this context, we examine systems not only during their operation but throughout their lifecycle, from design and development (with an emphasis on modeling, testing, simulation, and formal verification) to long-term monitoring of their performance and reliability.
Our work combines fundamental approaches with practical studies, aiming to provide innovative and robust solutions that enhance the reliability, predictability, and performance of systems, particularly in aerospace, transportation, energy, and critical infrastructure sectors.
Research in this area covers several key axes. We develop advanced methods for software testing, focusing on early defect detection and safety property validation. We also use safety arguments and formal verification to assess and quantify confidence in systems. Our research includes the study and scaling of real-time systems to meet the performance and responsiveness requirements of critical applications. Finally, we address these issues from the perspective of resilience and quality of service (QoS) compliance, as demonstrated by our work on proactive and adaptive strategies for managing QoS in the cloud continuum to optimize the performance of distributed systems.
Distributed Algorithms
Research in this area focuses on the design and analysis of distributed algorithms in computer networks and distributed systems. The scope is broad, ranging from theoretical studies of the properties of certain distributed algorithms (e.g., consensus) based on communication graphs to more applied research on parallel algorithms, federated learning, and distributed resource allocation in cellular networks, data center networks, and LPWANs. Major results have been achieved, particularly in fast local rerouting in networks and in measuring and improving the performance and robustness of Internet routes.
Methodologically, our research is based on a wide range of theoretical tools, including graph theory and mathematical optimization, as well as more original approaches such as combinatorial topology, stochastic optimal control, probabilistic analysis, and game theory. The emphasis is on the theoretical analysis of algorithm properties and the derivation of worst-case performance guarantees. However, experimental validation of the proposed algorithms is not neglected; our work relies on either in-vitro data from experimental platforms or in-vivo measurements from operational networks and systems.
AREAS OF
RESEARCH AND APPLICATIONS
Our research focuses on systems and applications with stringent requirements in terms of quality of service, real-time constraints, dependability, resilience, and security.
DISCIPLINARY FIELDS
COVERED IN OUR DEPARTMENT
DEPARTMENT TEAMS
The activities of the RISC department are conducted within two teams, TRUST and SARA, whose complementary research areas address the diverse challenges posed by the heterogeneity, dynamism, and criticality of processing and communication infrastructures and systems.

trust
A computing system is said to be "trustworthy" if it delivers a service in which users can have justified confidence. The TRUST team is interested in the methods, tools and processes that enable trust to be justified. *TRUST was created …
Latest publications
2026
Conference papers
Other documents
Reports
Preprints, Working Papers, ...
2025
Journal articles
Book sections
Conference papers
Other documents
Reports
Philippe Owezarski. D7.1 Architecture V1. LAAS-CNRS. 2025. ⟨hal-05337335⟩
Preprints, Working Papers, ...
Gersende Fort, Marcelo Pereyra. Monte Carlo. 2025. ⟨hal-05166306⟩
Céline Comte, Isaac Grosof. Graph-Based Product Form. 2025. ⟨hal-04956887v2⟩
2024
Journal articles
Books
Conference papers
Other documents
Proceedings
@softwareversion
Reports
Preprints, Working Papers, ...
THESIS / HDR
2025
2024
Zheng Zhou, Thèse: IoT omniprésent grâce aux communications spatiales
2023
Clément Cassé, Thèse: Prévision des performances des services Web en environnement Cloud
2022
2021
Kokouvi Benoit Nougnanke, Thèse: Vers un management basé ML des Réseaux SDNs
Clovis Anicet Ouedraogo, Thèse: Sur la gestion de la QoS dans les plates-formes IoT compatibles NFV
2020
Quentin Ricard, Thèse: Détection autonome de trafic malveillant dans les réseaux véhiculaires
Imane Oussakel, Thèse: Métrologie et management des réseaux cellulaires 4G/5G
Santiago Duran, Thèse: Allocation de ressources avec environnements observables et non-observables
2019
2018
Nicolas Seydoux, Thèse: Vers une gestion intelligente des données de l'Internet des Objets
Gilles Roudiere, Thèse: Détection d'attaques sur les équipements d'accès à Internet
2017
2016
Ikbel Guidara, Thèse: Choix efficace du temps et du QoS pour la composition du service
DEPARTMENT NEWS